Kerberos is a service that provides mutual authentication between users and services in a network. This refers to the LDAP server not.

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony
The Kerberos implementation found within Microsoft Active Directory is based on the Kerberos Network Authentication Service V5 which is detailed in RFC 4120.

Kerberos. Initially Kerberos was developed and deployed as part of the Athena project. Kerberos is available in many commercial products as well. Kerberos excels at Single-Sign-On SSO which makes it much more usable in a modern internet based and connected workplace.
Before you begin. You can create a Kerberos service principal name and keytab file by using Microsoft Windows IBM i Linux Solaris Massachusetts Institute of Technology MIT and zOS operating systems key distribution centers KDCs. If a non-authorized user has access to the Key Distribution Center the whole authentication system is compromised.
Once the request arrives on-premises the Azure AD Application Proxy connector issues a Kerberos ticket on behalf of the user by interacting with the local Active Directory. The issues are primarily related to the legacy support in Kerberos when Active Directory was released in the year 2000 with Windows Server 2000. Kerberos is an authentication protocol that is used to verify the identity of a user or host.
Contributing to the MIT Kerberos Documentation. While Kerberos v4 still has limited use in AFS environments it. Kerberos is adopted by a huge number of industries so any new weaknesses in its security protocol or in underlying modules are quickly corrected.
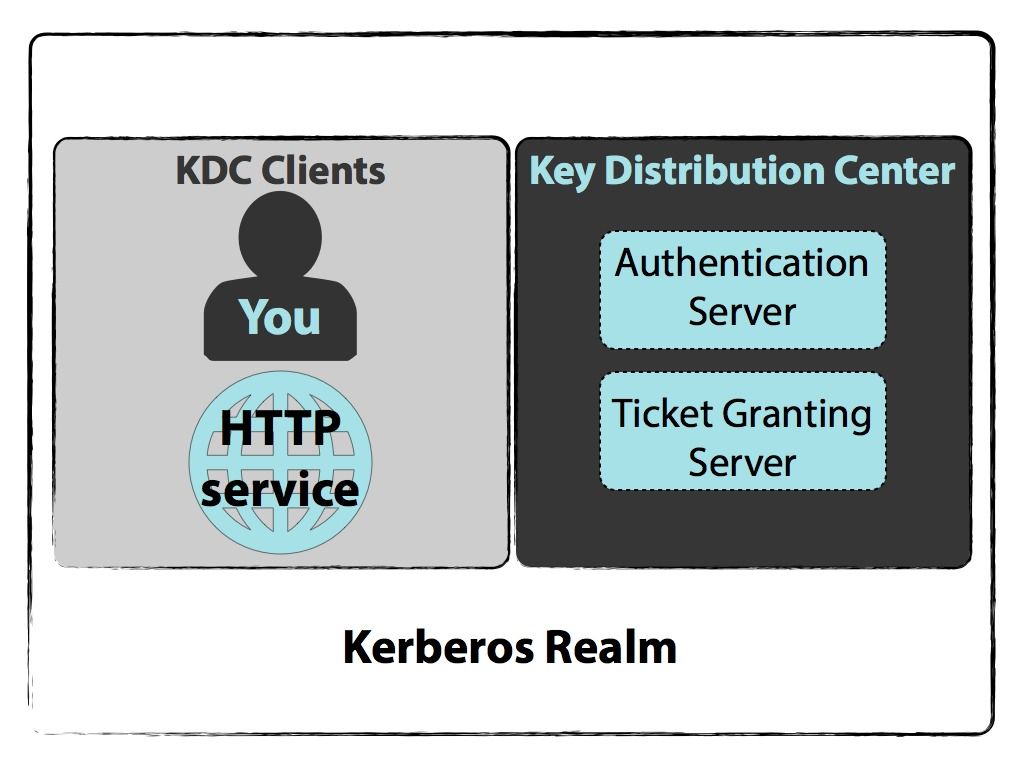
Kerberos can only be adopted by Kerberos aware applications. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. The kerberos principal has to match the FQDN of the LDAP server.
In the next phase a request is. This version of the Kerberos service and protocol was version 4. Microsoft expanded upon the base protocol specification adding a number of extensions to the protocol MS-KILE to implement behaviors and features specific to Active Directory and the Windows operating system.
This topic contains information about Kerberos authentication in Windows Server 2012 and Windows 8. In Kerberos Authentication server and database is used for client authentication. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users.
Protocols and file formats. Kerberos is a network authentication protocol. Each user and service on the network is a principal.
Make sure the DNS CNAME matches your hostname and that there is no ambiguity in your etchosts file. How to build this documentation from the source. Kerberos authentication events could be logged on any DC in the domain.
ManageEngine ADAudit Plus is an Active Directory auditing tool that can help monitor user logon activity using Kerberos authentication events. This process is referred to as Kerberos Constrained Delegation KCD. A centralized tool to monitor all the events will reduce the load immensely.
An Active Directory server is required for default Kerberos implementations. The main components of Kerberos are. With SSO you prove your identity once to Kerberos and then Kerberos passes your TGT to other services or machines as proof of your identity.
The KDC uses the domains Active Directory service database as its account database. Passwords can be brute-force cracked or stolen by phishing attacks. The weaknesses of Kerberos are.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. This task is necessary to process SPNEGO web or Kerberos authentication requests to WebSphere Application Server. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users identities.
An administrator would have to monitor events on each DC which is an excessive amount of work. To make changes to Microsoft Windows Active Directory you must have. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet.
The Windows Server operating systems implement the Kerberos version 5 authentication protocol and extensions for public key authentication transporting authorization data and. A free implementation of this protocol is available from the Massachusetts Institute of Technology. It could be a problem to rewrite the.
Also keep in mind the curiously named sasl-host line in your slapdconf. For plugin module developers. The weakest link in the Kerberos chain is the password.
Microsofts Kerberos implementation in Active Directory has been targeted over the past couple of years by security researchers and attackers alike. The Kerberos Key Distribution Center KDC is integrated with other Windows Server security services running on the domain controller. This legacy support is enabled when using Kerberos RC4 encryption.
It is popular both in Unix and Windows Active Directory environments. The Kerberos delegation flow in Azure AD Application Proxy starts when Azure AD authenticates the user in the cloud.

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Kerberos Art From Soul Sacrifice Art Artwork Gaming Videogames Gamer Gameart Conceptart Illustrat Fantasy Creatures Mythical Creatures Creature Concept

Kerberos Architecture Computer Help Windows Server Microsoft

Kerberos Web Graphic Design Vintage Graphic Design Poster Design

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Kerberos Explained Security Companies Band Patches Microsoft

Artist Tomasz Jedruszek Aka Morano Title Transcendent Kerberos Card Unknown Greek Mythological Creatures Mythological Creatures Werewolf Art

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Cerberus Or Kerberos In Greek And Roman Mythology Is A Multi Headed Usually Three Headed Dog Or Hel Greek And Roman Mythology Greek Mythology Greek Myths

Kerberos Architecture Computer Help Windows Server Microsoft

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Anime Armor Concept Dieselpunk

What Is Kerberos And How It Works Social Media Infographic Computer Network Infographic




0 σχόλια:
Posting Komentar